The American television series Mr. Robot introduces its viewers to a lot of hacking attacks, techniques, and tools. Most of it is based on actual methods and hardware, even if it is presented as far easier to do on the show than in real life. One thing the show portrays as a common, almost pedestrian attack technique is keylogging.
You need to know about keylogging, because it really is as common, easy to do, and critical to the success of criminals as it is on the TV show. That’s because the targets of attacks that involve keylogging are, well, just about anyone and everyone. And you wouldn’t even know that it’s happening.
How it works
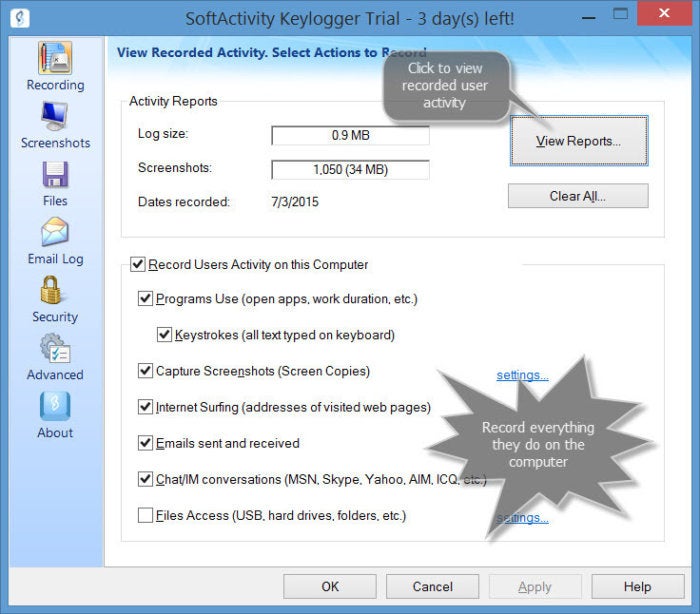
Keylogging, formally called “keystroke logging,” is exactly what it sounds like: It’s when a user’s keystrokes on a computer, tablet, or phone are recorded and tracked. This is sometimes done in an IT monitoring environment, or for studying human-computer interaction. Even Windows 10 has a creepy keylogger, to collect your info for… reasons. Fortunately, you can turn it off.
They’re also used by law enforcement. The FBI brought down Philadelphia mob boss Nicodemo Scarfo Jr. in 1999 when it installed the Magic Lantern keylogger via a Trojan. The spyware recorded his every keystroke, which the Feds were able to use to piece together their case. In 2007, the DEA used a keylogger to take down an MDMA (Ecstasy) lab.
But keylogging is more commonly done for nefarious reasons—without the user’s consent or knowledge that everything they type is being surveilled, and saved for later by whoever is spying on them.
The threat to you
Obviously criminals use keyloggers. They scrape up passwords, credit card and banking information, personal details, and more, to use in identity theft and other malicious deeds. Think about what you type every day that reveals sensitive information, like your bank account, and you can easily see what’s so worrying about keyloggers.
But thanks to commercial spyware companies, everyone is a potential victim of keylogger spying. These companies take digital spying tools, typically used by actual government spies and malicious hackers, and package them into easy-to-use bundles. These are marketed and sold to parents who want to monitor children, suspicious spouses, nosy employers, and more.
Of course, they’re purchased and used by more than that, and for a lot of creepy and unethical purposes. A recent expose showed that “ordinary people—lawyers, teachers, construction workers, parents, jealous lovers—have bought malware to monitor mobile phones or computers, according to a large cache of hacked files from Retina-X and FlexiSpy, another spyware company.” The tools enabled easy keylogging for anyone with $50 to spend.
The cache of hacked documents also revealed that the spyware companies had terrible security themselves, making it trivial for attackers to obtain the keylogging records of all the people its spyware had tracked.
So that’s one way you can be infected by keylogging software—any creep, jealous lover, nosy boss, cop, or anyone who purchases and installs it on your computer or device. Keyloggers are spread in same ways you can be infected by malware or viruses. Meaning, you get them when you engage in bad security practices. Like, leaving your phone or computer around with no PIN or password. Visiting infected websites, or clicking on tainted ads. And, as you might expect, opening attachments from people you don’t know.
Just this past April, a massive spam campaign was going around spreading a keylogger that collected victims’ keystrokes and sent them back to a server under the control of the spammers. It was spread by sending out a password protected Word document that, once you unlocked it, installed the infection.
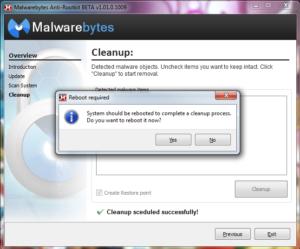
Detecting a keylogger is difficult. One sign that your keystrokes may be logged include your mouse or keystrokes pausing as you type or mouse, or they dont show up onscreen as what you are actually typing. You can buy anti-keylogger software, which supposedly scramble your keystrokes, but these programs don’t detect or remove the keylogger from your system.
If you think you’re being keystroke logged, you’ll need antivirus software designed to find and delete the undetectable type of infection called “rootkit malware.” These standalone scanners can be found at all the major reputable companies such as Malwarebytes, Kaspersky, Sophos, McAfee, and F-Secure.
Keyloggers aren’t going away anytime soon; they’re practically as common as dirt in the world of spying and crime. They’re a good reminder to trust our instincts, at least for those of us whose instincts were shaped by a different TV show than Mr. Robot. A show that encouraged us to “trust no one.”
Sources: pcworld
Hey My Readers and Visitirs If You Like Us or Our Web Site Please Share and Link back To My Site ... Take Care .,.,.

























.png)
0 comments:
Post a Comment